There are two main sides to every product or a service that is out there in a market. One is advantages and the other is disadvantages of the product or the service. Such does not however deter people from purchasing and using them. In the same way, as virtual private networks provide security for data and information on the web, they also have their shortcomings. The realization of a problem is a key factor to improving the product or the service and fixing the errors. The following is an outline of the most common defects of VPNs.
VPN fingerprinting is considered as one of the most common error the service encounters. However, the VPN service provider considers this not a threat at all. Fingerprinting gives potential evil doers a handful of important data, which includes the general device model and the version of the package with its details as well. The information may therefore enable an attacker to find an easy way around a client’s other credentials and eventually possible hacking.
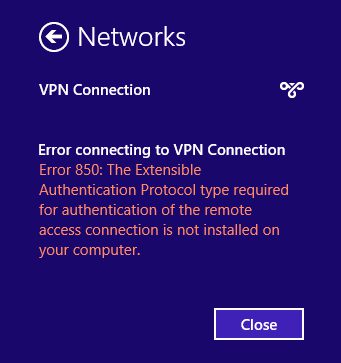 Another thing is that, many VPNs servers lack account lockout systems. Generally, most purposeful operating systems block an account after a user has entered a few incorrect login attempts, and refer them to a help page where they are supposed to verify a few details before receiving an aid. This means that someone with an idea of the VPN user’s login details might therefore, after a few trials be able to crack the account.
Another thing is that, many VPNs servers lack account lockout systems. Generally, most purposeful operating systems block an account after a user has entered a few incorrect login attempts, and refer them to a help page where they are supposed to verify a few details before receiving an aid. This means that someone with an idea of the VPN user’s login details might therefore, after a few trials be able to crack the account.
There is as well the error of default configurations, where sometimes they could be poor. Mainly, the default configurations focuses on the user’s smooth network accessibility, who in turns entrusts the VPN servers with all their details and expects them to have everything in place, hence worries not about their security. They believe that a threat could only arise in case of hacking. As the default configurations have many ciphers and modes supporting them, a user could configure their own systems to use higher ciphers, surpassing traffic and earning them almost invisible. On the other hand, a person having a direct or an indirect access to a client’s system might as well re-configure it, making it slower than usual, hence vulnerable to easy hacking. This is because it is virtually impossible to check the cipher’s encryption and the tunnel mode at the end of every connection. In case of an attack from without the client’s system, their VPNs work same as before, and that goes without a notice.
Sometimes, the VPNs servers may incur an error, due to the insecure storage of their client’s credentials. Many VPNs service providers offer the storage of their client’s crucial details including the username and the password. This service is mostly viewed as the default setting and enhances easy navigation of the VP Networks. While this is the case, security risks are overlooked and in one time or the other, common errors may arise. The risks often emanate from storage of unencrypted username in the registry or in a file, whereby a potential hacker with an access to the user’s system could easily get the user name.